What Is Fiber Optic Intrusion Detection and How Does It Work?
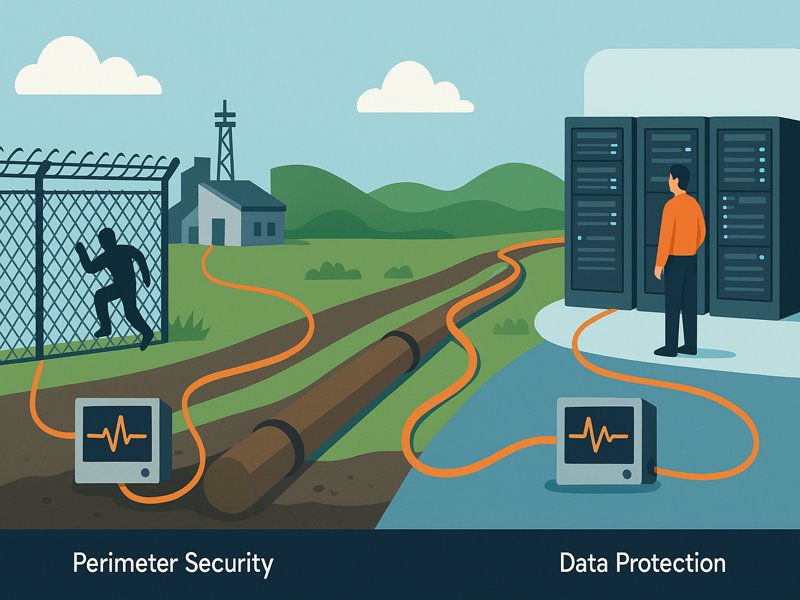
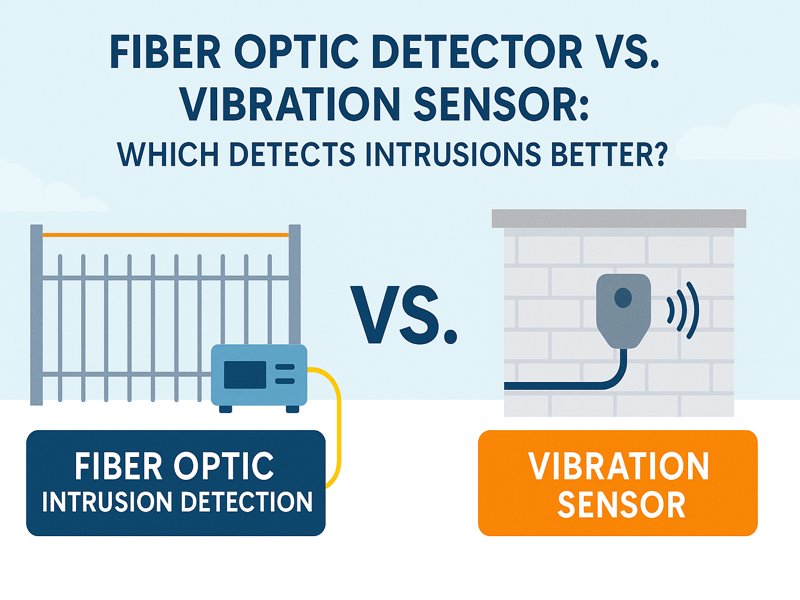
Fiber optic intrusion detection uses specialized cables to sense and report any unauthorized access or disturbance along a protected area. You can think of these cables as a sensitive tripwire or a microphone that listens for unusual vibrations. Unlike traditional electronic sensors, fiber optic systems can detect disturbances over long distances and remain reliable even in challenging environments. You gain better protection because these systems sense tiny changes in the fiber, making them less likely to miss an intrusion. Key Takeaways Fiber optic intrusion detection uses light signals to sense disturbances, making it more reliable than traditional electronic systems. These systems can cover long distances and detect even small changes, ensuring better security for sensitive areas. Advanced algorithms help reduce false alarms, allowing the system to focus on real threats while ignoring harmless events. You can use fiber optic systems for various applications, including perimeter security, infrastructure protection, and data centers. Knowing how this technology operates enables you to select the best option for efficiently safeguarding your assets. Intrusion Detection Overview What It Is You can think of fiber optic intrusion detection as a security system that uses light instead of electricity to sense threats. These systems use fiber optic cables to monitor for changes caused by physical disturbances. When someone tries to climb a fence, cut a cable, or tamper with a protected area, the system detects changes in the light signals traveling through the fiber. This method sets fiber optic systems apart from traditional intrusion detection technologies, which often rely on electronic signals or analyze network traffic. Fiber optic systems stand out because they: Transmit light signals through cables, not just electronic signals. Detect disturbances by monitoring changes in light, not just electrical changes. Respond to physical interactions, such as vibrations or pressure, which alter the light signal. You can find several types of fiber optic intrusion detection systems, each designed for specific needs. The table below shows some popular options and their features: System Type Features Aura Ai-X Data-driven technology with deep learning reduces nuisance alarm rates while maintaining high detection probability. Secure Fence Efficient on a variety of fence types, such as palisade, chainmesh, chain-link, and weldmesh. Secure Point Dual zone system with high sensitivity and low nuisance alarms, adaptable to almost all fence types. Aura Ai-XS Fence-mounted sensing up to 10 km, with precise intrusion detection within ±2 m. Aura Ai-XS (powered by FFT ATLAS) Continuous monitoring and maintenance for optimal performance of the intrusion detection system. Purpose You use fiber optic intrusion detection to protect sensitive areas from a range of threats. These systems help you detect: Unauthorized access, such as cable tapping or attempts to breach a perimeter. Suspicious activities, including unusual movements or behaviors near protected zones. Physical damage to cables can create vulnerabilities and risk data breaches. Organizations choose fiber optic intrusion detection for several reasons. The table below outlines the main objectives: Objective Description Accurate detection of intrusions Ensures that any unauthorized access is identified promptly. Resilience against tampering The system is designed to trigger alarms if the cables are cut or tampered with. Low false alarm rates Capable of distinguishing between real threats and environmental factors, reducing unnecessary alerts. Quick response times Real-time detection allows for immediate action to be taken in case of a security breach. Cost-effectiveness Although initial costs may be higher, long-term savings on maintenance and reliability are significant. Scalability It can be deployed over large areas, making it suitable for extensive perimeters. Reliable performance Continuous monitoring ensures consistent security coverage. You measure the effectiveness of these systems by looking at several factors: Reliability, which means the system works even during outages. Accuracy, which helps you avoid false alarms. Capabilities, so you can keep up with the latest detection features. Maintenance, since low-maintenance systems save you time and money. Coverage, which ensures you detect intrusions precisely. Integrations, so your system works well with other security technologies. Fiber optic intrusion detection gives you a reliable way to secure perimeters. The cables detect stress or breaks when someone tries to breach the area. This technology resists interference, making it a strong choice for organizations that want dependable security. How It Works Sensing Disturbances You rely on fiber optic cables to act as sensitive detectors along your perimeter. These cables use light to sense even the smallest physical changes. When someone tries to climb a fence, dig near a buried cable, or tamper with a protected area, the cable picks up the disturbance. The system then analyzes these changes in the light signal to determine if an intrusion has occurred. Fiber optic cables can detect several types of disturbances in real-world security scenarios: Vibration Detection: The system senses vibrations caused by footsteps, digging, or cutting. Technologies like fiber Bragg gratings (FBG) and distributed acoustic sensing (DAS) help you secure the physical layer of your perimeter. Polarization Changes: Some systems use polarization-sensitive techniques to spot changes in the way light travels through the cable. This helps you identify disturbances that might not cause strong vibrations. Interferometric Methods: Advanced systems use interferometers, such as Mach–Zehnder and Michelson types, to pick up subtle vibrations. These methods work well for perimeter security and can detect even light touches. Tip: Fiber optic cables are perfect for isolated locations or expansive perimeters because they can detect disruptions over long distances. Environmental factors can sometimes mimic intrusion attempts. You need to understand how wind, rain, or even the movement of a fence can affect detection. The table below shows how these factors impact the system and what you can do to reduce false alarms: Environmental Factor Impact on Detection Mitigation Techniques Wind Creates vibrations that may trigger false alarms Environmental disaggregation, advanced pattern recognition Rain Can cause disturbances similar to intrusion attempts Frequency filters, advanced detection algorithms Fence Fabric Movement Excessive movement can lead to nuisance alarms Proper maintenance, software-defined zones You may rely on your system to overlook innocuous occurrences and concentrate on actual risks by utilizing sophisticated detection and mitigation strategies. Signal Processing After the fiber