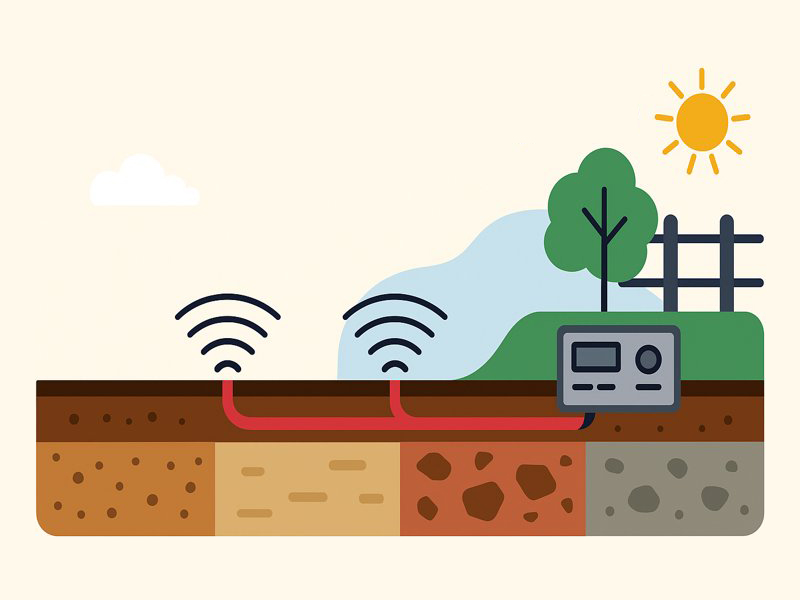
Modern security solutions require discreet, intelligent, and resilient systems for protecting critical infrastructure, military zones, data centers, airports, and estates. The Buried Cable Intrusion Detection System is one of the most reliable and concealed perimeter protection methods.
Unlike above-ground barriers, buried cable systems offer an invisible detection field, sensing disturbances from footsteps, digging, or vehicle movement. The system’s effectiveness relies on four key components:
- Buried Sensor Energizer
- Transmitting Sensor Cable
- Receiving Sensor Cable
- Control Host (Central Processing Unit)

Buried Sensor Energizer: The Source of Detection Field
At the core of any buried cable intrusion detection system is the Buried Sensor Energizer, which acts as the source of energy that powers the detection field. This component generates and transmits a low-frequency electromagnetic signal through the transmitting sensor cable.
Key Functions:
- Signal Generation: Produces a stable, low-voltage signal that radiates into the surrounding soil between the two buried cables.
- Power Distribution: Supplies energy to both the transmitting and receiving cables, ensuring consistent operation.
- Field Creation: Establishes a symmetrical electromagnetic field between the cable pair. Any object entering this field disturbs the balance and is flagged as a potential intrusion.
- Synchronization: Keeps signal timing and amplitude consistent for accurate detection and minimal noise.
Technical Features:
- Operates on low voltage for safety and efficiency.
- Supports a wide range of soil types, including sand, gravel, clay, or asphalt.
- Made to function in conditions like freezing ground, intense rain, and extreme temperatures.
- May include self-diagnostics and built-in EMI (Electromagnetic Interference) protection.
The energizer is typically mounted in a weatherproof enclosure near the protected perimeter and connected to both the transmitting and receiving sensor cables.
Transmitting Sensor Cable: Creating the Electromagnetic Detection Zone
The Transmitting Sensor Cable works in tandem with the buried sensor energizer to emit the electromagnetic field into the surrounding ground. It is usually buried in parallel with the receiving cable, forming a detection zone between them.
Role in the System:
- Signal Transmission: Carries the electromagnetic signal generated by the energizer into the ground.
- Field Coverage: Establishes one boundary of the detection field.
- Field Strength: Designed to maintain consistent signal output, even in challenging terrain or variable soil conductivity.
Design Considerations:
- Buried at a depth of approximately 20–30 cm, depending on the soil and threat level.
- Typically installed in a parallel or figure-8 layout to shape the detection zone effectively.
- Encased in durable, UV- and moisture-resistant jackets to withstand long-term burial and environmental exposure.
- May include shielding layers to reduce interference from nearby electronic equipment or lightning strikes.
High-quality transmitting cables are engineered to minimize signal loss, reduce false alarms, and provide long-term stability over years of operation.

Receiving Sensor Cable: Detecting Intrusions with Precision
While the transmitting cable sends signals out into the soil, the Receiving Sensor Cable captures the disturbed signal when the detection field is disrupted. It is responsible for measuring variations in the returning electromagnetic field caused by an intruder entering the protected zone.
Primary Responsibilities:
- Signal Detection: Monitors and receives the return signal influenced by soil vibrations, pressure changes, or movement.
- Signal Deviation Analysis: Detects variations in amplitude, frequency, and waveform caused by disturbances.
- Transmission to Control Host: Sends the captured data to the control host or processor for further analysis and alarm decisions.
Technical Highlights:
- Installed parallel to the transmitting cable, with precise spacing to define the width and sensitivity of the detection zone.
- Supports bidirectional communication in some systems, allowing diagnostic feedback.
- Often features multi-layer shielding to ensure signal clarity and noise immunity.
- Protected against rodent damage, corrosion, and soil acidity.
The effectiveness of the buried cable system largely depends on the calibration and alignment between the transmitting and receiving sensor cables. Proper installation ensures uniform detection sensitivity across the entire perimeter.
Control Host: Central Intelligence of the System
The Control Host—also referred to as the Processor Unit or Central Processing Module—is the brain of the buried intrusion detection system. It continuously analyzes incoming signals from the receiving cable, determines whether a disturbance is a real threat or an environmental anomaly, and activates alarms when necessary.
Core Functions:
- Signal Interpretation: Processes analog signals into digital data using advanced algorithms or machine learning models.
- Intrusion Recognition: Differentiates between human footsteps, vehicle vibrations, animal movement, and natural phenomena.
- Alarm Generation: Activates sirens, lights, video surveillance, or remote alerts in the event of intrusion.
- User Interface: Provides a GUI or dashboard for real-time monitoring, system diagnostics, and configuration.
Additional Capabilities:
- Zone Management: Divides the protected area into multiple detection zones (e.g., 100m per zone), enabling precise intrusion localization.
- Event Logging: Records alarms, faults, and user actions for audit trails or forensic investigation.
- Remote Access: Allows off-site configuration and monitoring via LAN, WAN, or cloud platforms.
- System Health Monitoring: Detects cable faults, power issues, or communication failures automatically.
The control host may be integrated with a broader security infrastructure, including video surveillance (CCTV), access control systems, and SCADA platforms, to create a unified perimeter protection ecosystem.
How These Components Work Together
The interaction between these four components is what enables a buried cable intrusion detection system to perform reliably in real-world conditions:
- The Buried Sensor Energizer generates a stable electromagnetic signal.
- This signal travels through the Transmitting Sensor Cable, forming a detection zone between itself and the receiving cable.
- When an intruder walks over or near the detection field, the Receiving Sensor Cable captures the distorted signal.
- The Control Host analyzes this data in real-time, filters out environmental noise, and triggers alarms only when a legitimate threat is detected.
This closed-loop system is appropriate for both high-security and civilian applications since it guarantees excellent accuracy with few false alarms.
Advantages of Using These Components
Understanding the function of each component allows security professionals to appreciate the system’s robustness. Here’s why this setup is widely trusted:
- Invisible Protection: No above-ground hardware, making it tamper-resistant and aesthetically clean.
- Scalable Design: Modular architecture allows extension up to several kilometers.
- All-Weather Performance: Functions reliably in rain, snow, heat, and frost.
- Low Maintenance: Once installed, components require minimal servicing.
- High Detection Accuracy: Can identify intrusions with up to 1–5 meter localization precision.
Final Thoughts
A Buried Cable Intrusion Detection System’s effectiveness depends on its components: the Energizer, Transmitting Sensor Cable, Receiving Sensor Cable, and Control Host. Together, they provide real-time, invisible, and accurate alerts, ensuring perimeter security without notifying intruders. Ideal for military, airport, solar, or corporate facilities, a well-designed system keeps your perimeter secure.